Big Phish

Last month’s attack on the Ronin Network was the largest crypto hack ever, but despite the amount, the story didn’t generate anywhere near as much interest as the former #1, Poly Network.
However, the Ronin case came back into the spotlight after the FBI announced that they believe The Lazarus Group, a collective of North Korean state-sponsored hackers, are responsible for the theft.
Yesterday, the Cybersecurity and Infrastructure Security Agency (CISA) published a report with examples of the methods used by the group, also known as Advanced Persistent Threat (APT) 36.
In the report, they state:
”North Korean state-sponsored cyber actors use a full array of tactics and techniques to exploit computer networks of interest, acquire sensitive cryptocurrency-intellectual property, and gain financial assets.”
We wonder, how many of our stories can be linked to North Korea?

The Lazarus group, and specifically the financially-focussed BlueNoroff sub-group, has a long history, including ties to the Sony hack (2014), the Bangladesh Bank robbery (2016), in which >$100M was transferred out of the Federal Reserve Bank of New York via the SWIFT network, and the WannaCry ransomware attack (2017).
In the cryptosphere, the group’s attacks have tended to focus on CEXs, including Kucoin, Liquid.com, NiceHash and Bithumb, using social engineering to obtain access to private keys.
However, more recently, a move towards DeFi has been noted.
Phishing attacks are common in DeFi, especially among the NFT community, with tales of rookie (and veteran) users alike constantly being targeted via Discord and Telegram.
Back in 2020 we spoke to Hugh Karp of Nexus Mutual about his experience losing $8M, and last month, DeFiance Capital’s Arthur Cheong lost ~$1.7M.
In Ronin’s case, though, the entire network was compromised, in no small part due to a worryingly small validator set.
The >$600M were taken from the network’s bridge after attackers gained access to 5 of just 9 validator signatures securing the network.
With four of the validators all coming from the same organisation (Sky Mavis), the set-up must have already looked promising for a potential phishing campaign.
But given that the fifth signature needed for a majority was accessible via an old, but still active, arrangement between Sky Mavis and Axie DAO to ease network traffic, it was only a matter of time until Lazarus found their way in.
The level of sophistication demonstrated by the Lazarus Group’s social engineering campaigns is remarkable. As this blog entry from cybersecurity firm Kaspersky states:
“If there’s one thing BlueNoroff has been very good at, it’s the abuse of trust.”
The article goes on to detail an attack vector via a malicious document shared via Google Drive. Other novel vectors include browser-in-the-browser (BitB) attacks, Google Docs comments, and even developing a malicious wallet application.
A longer list of examples, with screenshots, can be found in this thread by Taylor Monahan.
While the specifics may vary, the key to the successful delivery of a payload is minimising scrutiny, achieved by knowing intricate details of the target organisation.
“The goal of the infiltration team is to build a map of interactions between individuals and understand possible topics of interest. This lets them mount high-quality social engineering attacks that look like totally normal interactions. A document sent from one colleague to another on a topic, which is currently being discussed, is unlikely to trigger any suspicion. BlueNoroff compromises companies through precise identification of the necessary people and the topics they are discussing at a given time.”
Yesterday’s CISA report provides:
information on tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) to stakeholders in the blockchain technology and cryptocurrency industry to help them identify and mitigate cyber threats against cryptocurrency.”
It describes a series of malicious applications that are delivered via the spearphishing to employees disguised as “trading or price prediction tools”.
Observed payloads include updated macOS and Windows variants of Manuscrypt, a custom remote access trojan (RAT), that collects system information and has the ability to execute arbitrary commands and download additional payloads (see North Korean Remote Access Tool: COPPERHEDGE). Post-compromise activity is tailored specifically to the victim’s environment and at times has been completed within a week of the initial intrusion.
The report goes on to list some Indicators of Compromise and recommendations for mitigation, which include:
A cybersecurity aware workforce is one of the best defenses against social engineering techniques like phishing.
Both Kaspersky and Cheong have also warned teams in the industry to be especially vigilant, publishing some basic recommendations that organisations can take to protect themselves, such as using multisig wallets, hardware 2FA, and dedicated machines solely for crypto transactions.

As the crypto crimewave shows no sign of slowing, on-chain investigation companies such as Chainalysis are in high demand.
We asked Erin Plante, Senior Director of Investigations at Chainalysis, for their take on state-sponsored hacking in DeFi:
"The attribution of Lazarus to the Ronin attack underlines two trends in hacking. The first is the productivity of DPRK-affiliated threat actors and their exploitation of cryptocurrency. This is a national security concern considering they have stolen billions of dollars' worth of crypto and the UN has connected this activity to funding their nuclear program. The second trend is the need for better security for DeFi protocols. Almost 97% of all cryptocurrency stolen in the first three months of 2022 has been taken from DeFi protocols, up from 72% in 2021 and just 30% in 2020."
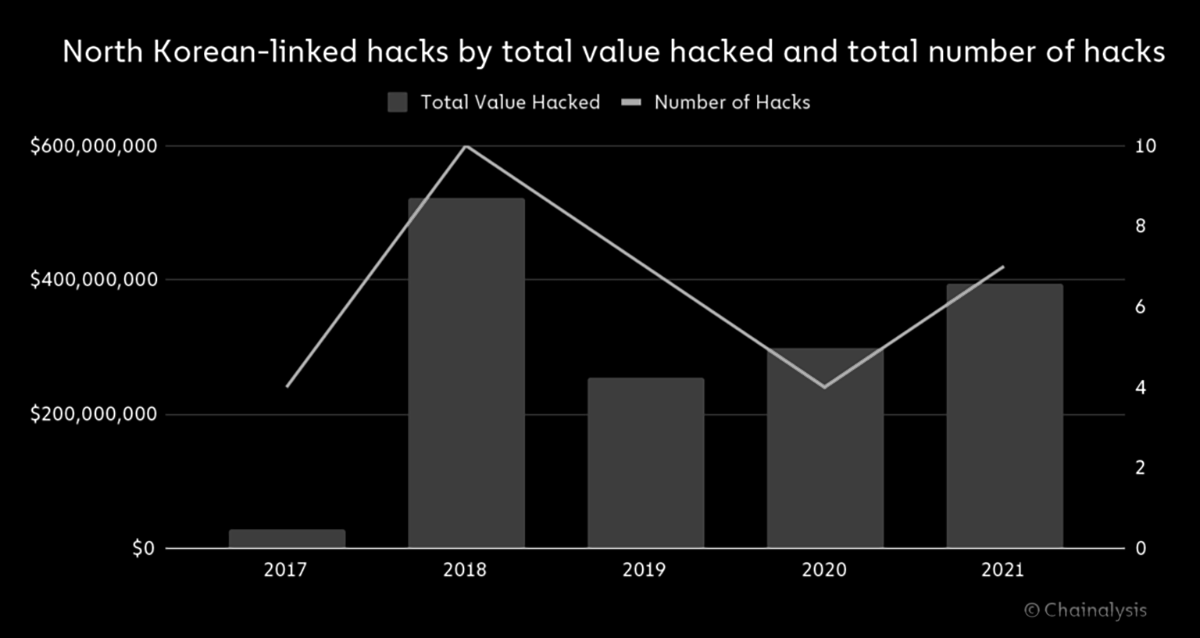
This detailed report, published by Chainalysis in January, sums up the various crypto heists attributed to North Korean hackers, starting all the way back in 2017.
With the ~$600M loot from the Ronin incident, 2022 has already been more profitable for DPRK than last year, and we’re not even halfway through.
But how will they launder the loot?
In addition to the unexpected use of CEXs, a route usually avoided due to KYC requirements, the report details the group’s increasing use of mixing services; they appear to be operating more cautiously with time, as crypto steadily moves into the mainstream.
The typical laundering process is as follows:
- ERC-20 tokens and altcoins are swapped for Ether via DEX
- Ether is mixed
- Mixed Ether is swapped for Bitcoin via DEX
- Bitcoin is mixed
- Mixed Bitcoin is consolidated into new wallets
- Bitcoin is sent to deposit addresses at crypto-to-fiat exchanges based in Asia —potential cash-out points
Chainanalysis also suggests that Lazarus may be sitting on funds, waiting for law enforcement attention to die down among an ever-growing exploit list.
Either way, it takes time:
”Of DPRK’s total holdings, roughly $35 million came from attacks in 2020 and 2021. By contrast, more than $55 million came from attacks carried out in 2016—meaning that DPRK has massive unlaundered balances as much as six years old.”
For such a large amount, though, it seems that the hackers are not willing to wait.
The Ronin funds are well on their way to being laundered, with Elliptic estimating that some $107M are already in the process.
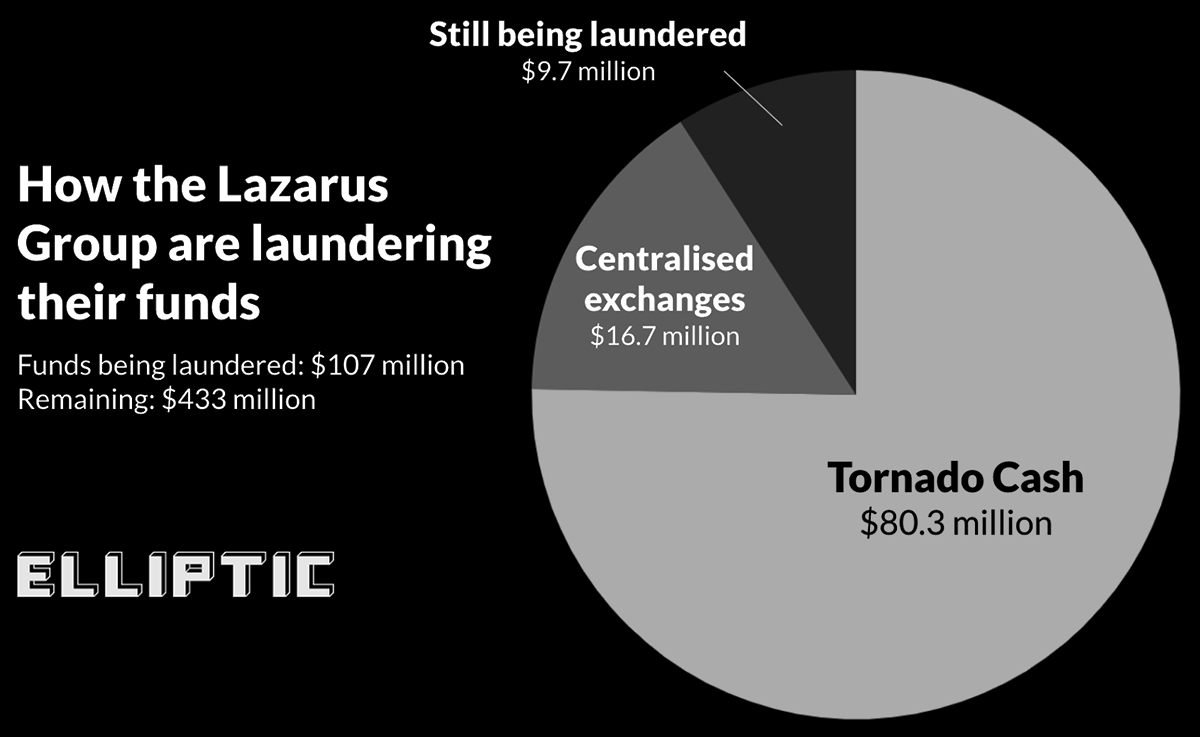
While the involvement of CEXs is somewhat non-standard for DeFi laundering, the clear preference for Tornado Cash comes as no surprise.
With all this law enforcement attention, and the key part that mixers play in washing stolen funds, Tornado Cash was bound to come under the spotlight sooner or later.
Thursday’s news also prompted a statement from the privacy tool (and hacker favourite) Tornado Cash, that an on-chain list of sanctioned addresses (maintained by Chainalysis and including the Ronin exploiter) would be unable to access the dapp.
However, given that the underlying smart contracts are immutable, not having access to a UI is unlikely to deter anyone capable of pulling off a DeFi heist, state-sponsored or otherwise.
Is this just a way to feign compliance and keep regulators at bay? Surely it can’t be that easy..
As their desperation increases, how far will our governments go to stamp out this alternate economy?

REKT serves as a public platform for anonymous authors, we take no responsibility for the views or content hosted on REKT.
donate (ETH / ERC20): 0x3C5c2F4bCeC51a36494682f91Dbc6cA7c63B514C
disclaimer:
REKT is not responsible or liable in any manner for any Content posted on our Website or in connection with our Services, whether posted or caused by ANON Author of our Website, or by REKT. Although we provide rules for Anon Author conduct and postings, we do not control and are not responsible for what Anon Author post, transmit or share on our Website or Services, and are not responsible for any offensive, inappropriate, obscene, unlawful or otherwise objectionable content you may encounter on our Website or Services. REKT is not responsible for the conduct, whether online or offline, of any user of our Website or Services.
you might also like...
Ronin Network - REKT
A new number one on the leaderboard. ~$624M stolen from Ronin Network, but nobody even noticed for 6 days. Will the attacker try to launder the loot?
