Stars Arena - REKT

In the arena, breaking things.
A double-whammy of embarrassing security blunders led to Stars Arena being drained of almost $3M (its entire TVL) on Saturday.
The Avalanche-based FriendTech clone, heavily shilled by the usual suspects, had been hit by an (economically unviable) exploit the previous day.
The team’s cringe announcement of a fix didn’t inspire much confidence that security was their primary concern:
THE EXPLOIT HAS BEEN FIXED.
BUT DON’T GET THIS WRONG WE ARE AT WAR.
The team brushed off the vulnerability as “throwing money away”, a sentiment repeated by Ava Labs’ CEO Emin Gün Sirer, who dismissed the incident as FUD (unsurprisingly, as he’d also spent last week relentlessly shilling the project).
While it may be surprising that Avalanche’s ecosystem ambassador would promote an unaudited, unverified fask-fork of a flash-in-the-pan SocialFi ponzi, the double-down after the second hack was more mindboggling still.
The amount lost is only $3m…
...something that SA can recover in about 10 days or so…
...the hack is a mere speed bump...
Presumably because this was the first time AVAX had been relevant in months, Sirer then continued to go to bat for the commpletely drained protocol as CT looked on in confusion.
Ever heard the phrase ‘stop digging’?

The first hack was down to a broken getPrice() function. However, the exploit required spending 4x the profit in gas to drain the contract, which lost just $2k before users (allegedly including the user who publicised the vulnerability) gave up.
The team announced the fix and the proxy was upgraded to a new (also unverified) contract.
Then, amidst the criticism of the team’s comms, came the second exploit, draining $2.9M.
The contract is unverified, but according to Beosin the attacker took advantage of a reentrancy vulnerability to insert a block height as the number of AVAX to send during the sellShares() function.
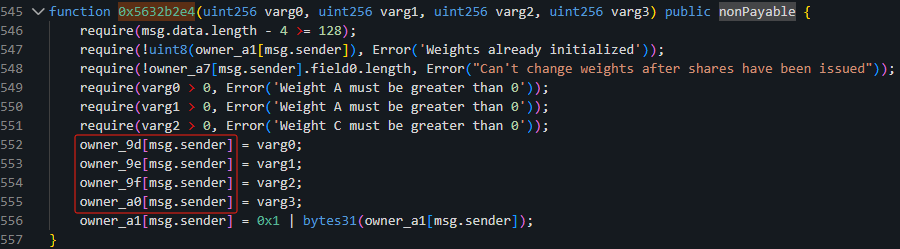
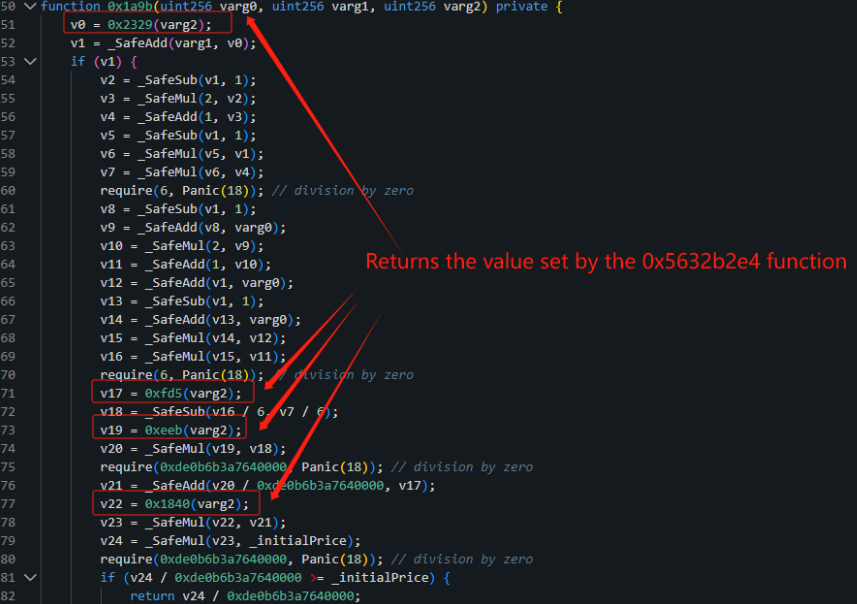
Hacker’s address: 0xa2Ebf3FCD757e9BE1E58B643b6B5077D11b4ad7A
As more attention was paid to the project, the hypocrisy of the team became clear, claiming "security is the core driving factor behind everything we do" whilst having access to users’ PKs and leaving their system wide open to DDOS.
Oh, and getting hacked twice of course…

As the summer’s FriendTech hype rapidly died away, our innovative industry did what it does best: launching a slew of clones, quick cash grabs which add nothing new.
Except vulnerabilities.
FriendTech itself has been hit by a wave of SIM-swap attacks with the last bull run’s easiest targets being made high priority.
Or perhaps we have simply reached the boating-accident-via-SIM-swap stage of the ponzi cycle.
As the scheme unwinds the userbase appears to be getting increasingly PvP by the day, but amidst the high-fee dumpfest the devs certainly aren’t complaining.
But as for Avalanche’s latest failed shill, who look to be planning a relaunch…
Will you be jumping back into the Stars Arena, anon?

REKT serves as a public platform for anonymous authors, we take no responsibility for the views or content hosted on REKT.
donate (ETH / ERC20): 0x3C5c2F4bCeC51a36494682f91Dbc6cA7c63B514C
disclaimer:
REKT is not responsible or liable in any manner for any Content posted on our Website or in connection with our Services, whether posted or caused by ANON Author of our Website, or by REKT. Although we provide rules for Anon Author conduct and postings, we do not control and are not responsible for what Anon Author post, transmit or share on our Website or Services, and are not responsible for any offensive, inappropriate, obscene, unlawful or otherwise objectionable content you may encounter on our Website or Services. REKT is not responsible for the conduct, whether online or offline, of any user of our Website or Services.
you might also like...
Platypus Finance - REKT 2
After three exploits in 8 months, Platypus is beginning to look like an endangered species. A flashloan attack has drained the Avalanche-based protocol of $2.2M. It’s been a rough week for Avalanche.
Platypus Finance - REKT
Evolution works in mysterious ways. Platypus Finance lost $8.5M to a flash loan attack on its recently-launched stablecoin. It’s a jungle out there... and, as ever, it’s survival of the fittest.
Snowdog - REKT
A “game theory experiment” or a new breed of rug pull? ~$18M snapped up by just the first two transactions of Snowdog’s buyback. Was it luck or inside information that led the top dogs to success?
