Socket - REKT

Infinite approvals… the ultimate leap of faith.
Socket’s Bungee bridge lost $3.3M yesterday to an attack draining addresses that had previously approved the SocketGateway contract on Ethereum.
Shortly after the alarm was raised, the team acknowledged the hack, having patched the vulnerability just 14 minutes after the attack began.
Wallet provider Rainbow also informed their users, as Socket’s contracts are used by the in-app bridging feature. They urged users to check whether their address was affected and revoke approvals via RevokeCash’s dedicated tool.
As the over $80M NYE attack on Orbit shows, bridges continue to be a prime target for blackhats, and must be subject to the highest levels of scrutiny whenever any changes are made.
Why did a known bug make it to production on a live bridge?

Credit: qckhp, Peckshield, Beosin
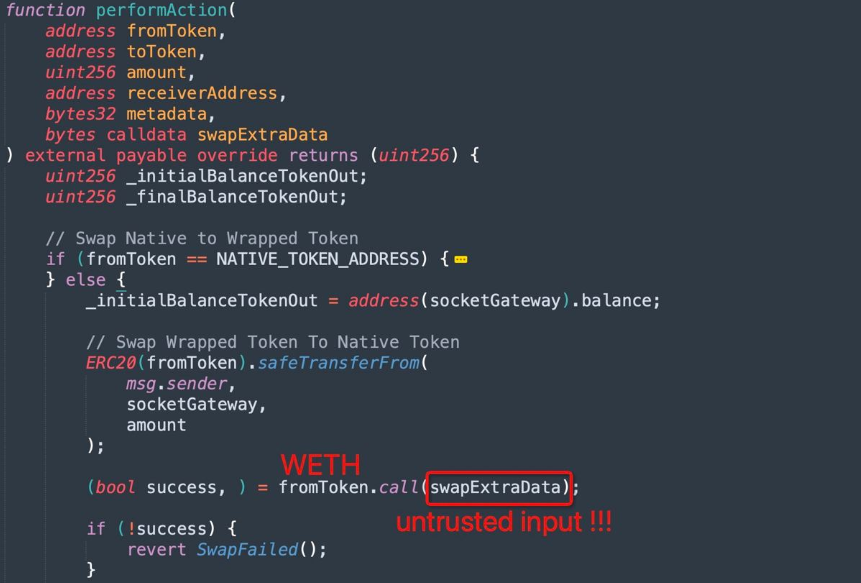
The attack was due to a lack of validation of user input contained in a new route added to the bridging contract three days prior to the exploit.
The vulnerable route’s contract itself neglects to validate the swapExtraData parameter, allowing an exploiter to inject a transferFrom call, and send approved assets from victim addresses to their attack contract.
As Beosin points out:
It did not consider the case where the caller transfers in 0 WETH, allowing the caller to specify other functions in the call and still pass the balance check.
Attacker’s address: 0x50df5a2217588772471b84adbbe4194a2ed39066
SocketGateway contract: 0x3a23f943181408eac424116af7b7790c94cb97a5
Socket contracts have audits by both Peckshield and Consensys Diligence. However, given that the new route was added just three days prior to the exploit, neither audit examined the vulnerable code.
Funds stolen include ETH, MATIC, WBTC, WETH and DAI totalling approximately $3.3M.
The stolen assets remain in the attacker's address, which has received a message threatening to dox the attacker if not paid off:
100 ETH and I'll throw away the timing analysis routing through FixedFloat that doxxes you. After 6 hours I go to Zach. Act swiftly.

Infinite approvals strike again.
Despite Bungee’s response that “Bungee doesn't request infinite approvals by default”, other protocols which route via the affected contract must subscribe to the UI before security mindset.
Otherwise, it’s hard to believe that so many users would be vulnerable.
With the biggest loss at over $600K and the five hardest-hit victims each losing over $100K, this will have been a costly lesson in approvals hygiene for some.
Without a regular revoking detox, token approvals sit waiting for a live (or forgotten) project to be exploited. And given that tokens are stolen directly from users’ wallets, there’s no need to have any funds deposited to fall victim.
However, all this could have simply been avoided by not making risky, unaudited upgrades to an existing bridge contract.
Have you checked your approvals lately, anon?

REKT作为匿名作者的公共平台,我们对REKT上托管的观点或内容不承担任何责任。
捐赠 (ETH / ERC20): 0x3C5c2F4bCeC51a36494682f91Dbc6cA7c63B514C
声明:
REKT对我们网站上发布的或与我们的服务相关的任何内容不承担任何责任,无论是由我们网站的匿名作者,还是由 REKT发布或引起的。虽然我们为匿名作者的行为和发文设置规则,我们不控制也不对匿名作者在我们的网站或服务上发布、传输或分享的内容负责,也不对您在我们的网站或服务上可能遇到的任何冒犯性、不适当、淫秽、非法或其他令人反感的内容负责。REKT不对我们网站或服务的任何用户的线上或线下行为负责。
您可能也喜欢...
Orbit Bridge - REKT
It wasn’t just fireworks blowing up on New Year’s Eve... Orbit Chain’s Ethereum bridge lost $81.5M. What will 2024 bring?
Hypr Network - REKT
What is this, a bridge hack for ants? Yesterday, Hypr Network lost $220k to a bridge exploit. Forking code can be risky, especially when devs aren't up to date with issues in the source.
Shibarium Bridge - REKT
The Shibarium devs are in the doghouse. A botched launch of Shiba Inu’s ETH L2 sees a total of $2.6M of user funds stuck in a faulty bridge. Memecoins are evolving... but why?
