Shezmu - Rekt

Shezmu's vault became the latest battleground where $4.9 million vanished faster than a mirage in the desert.
But in a twist worthy of a crypto thriller, the saga unfolded not with a bang, but with a negotiation.
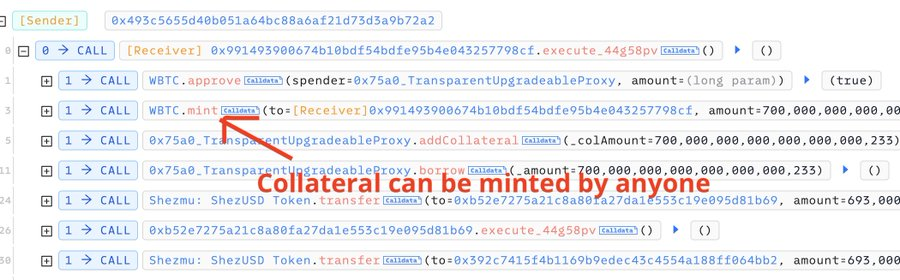
On September 20th, Shezmu found itself in the crosshairs of an opportunistic hacker who had stumbled upon a critical flaw - a vault accepting collateral that could be minted by anyone.
With this vulnerability, the attacker managed to borrow an arbitrary amount of ShezUSD, draining millions from the protocol.
Yet, in a move that would make even the most seasoned poker players sweat, Shezmu called the hacker's bluff.
They laid their cards on the table: return the funds for a 10% bounty and walk away scot-free, or face the full force of the law within 24 hours.
The hacker, unfazed, countered with a demand for 20%.
In a game of crypto chicken, Shezmu blinked first, agreeing to the 20% bounty.
In a world where code is law, but negotiation saves the day, who really holds the winning hand - the hacker with the loot, or the protocol with the flexibility to bend?

Chaofan Shou, co-founder of blockchain analytics firm Fuzzland, sounded the alarm:
"ShezmuTech has been hacked / rugged. ~$4.9M worth of $ShezUSD stolen."
The culprit? A vault with a gaping vulnerability - it accepted collateral that could be minted by anyone.
This fatal flaw allowed the attacker to borrow an arbitrary amount of ShezUSD, effectively printing money faster than Jerome Powell on a sugar rush.
Just 17 days before the exploit, on September 3rd, Shezmu had deployed a contract upgrade: 0x8db5356ec348a991adaadfd7f366d72eccafcb0113c7ac31f1dddde9c8c3f81e
Did this upgrade introduce the vulnerability? Or did it merely fail to patch an existing one?
In the fast-paced world of DeFi, even routine upgrades can become ticking time bombs.
A trail of addresses and transactions emerged, painting a clearer picture of the exploit:
Attack Contract: 0xEd4B3d468DEd53a322A8B8280B6f35aAE8bC499C
Shezmu Attacker (created contract):
0xA3a64255484aD65158AF0F9d96B5577F79901a1D
Attack Contract created: 0x39328ea4377a8887d3f6ce91b2f4c6b19a851e2fc5163e2f83bbc2fc136d0c71
The attacker didn't just stumble upon a vulnerability; they crafted a bespoke contract to exploit it.
Sometimes in the world of DeFi, your greatest threat might be the anonymous dev next door.
But even the most carefully laid plans can go awry in the volatile realm of crypto.
During the exploit, Chaofan Shou noticed something interesting:
“Due to low liquidity, these $4.9M worth of $ShezUSD are swapped to only $700K.”
Could a master heist have been foiled by market mechanics?
As news of the attack spread like wildfire through the crypto-sphere, Shezmu's team didn't waste a moment.
Within hours, Shezmu's team sprang into action, issuing a statement urging users to steer clear of the dApp while they investigated.
Shezmu reached out to the attacker with an offer they hoped couldn't be refused: a 10% bounty in exchange for the safe return of the funds.
The message was clear - play ball, and we'll call it a white-hat hack. Refuse, and face the full force of the law.
But our hacker wasn't about to fold so easily.
The on-chain conversation unfolded with surprising civility, considering millions were at stake.
Threats of legal action met with polite rebuttals, and in the end, a deal was struck.
Shortly after, the funds began trickling back.
Shezmu confirmed recovering the stolen funds, minus the agreed-upon bounty, and stated a post-mortem is forthcoming.
Stolen Funds Returned: 0x058a453abb03803aacfcc94cbeb410ceb56aa8aa2edb4ad3efa3e78522980cba
The community watched in real-time as a potential catastrophe transformed into a masterclass in crisis management.
In the aftermath, Shezmu emerged battered but not beaten.
But here's where the plot thickens. Remember that low liquidity mentioned earlier? Turns out, it might have been the key to this whole resolution.
As Chaofan Shou, our eagle-eyed first responder, pointed out:
"Due to low liquidity, these $4.9M worth of $ShezUSD are swapped to only $700K."
Suddenly, that 20% bounty on the full $4.9 million starts looking pretty attractive, doesn't it?
In the end, was it the threat of legal action, the allure of a hefty bounty, or a hacker's change of heart that saved the day?
Or perhaps, it was the cold, hard math of a liquidity crunch that turned our black hat white.

While Shezmu’s swift negotiation saved the day, it can't erase the glaring oversight in their security practices.
Shezmu failed to scrutinize their September 3rd contract upgrade, leaving the door wide open for an enterprising hacker.
In the end, was it skill or luck that kept Shezmu from total ruin?
Their hasty 20% bounty might have saved millions, but it's a band-aid on a bullet wound.
And the soundtrack to this all-too-familiar scene?
Cue the broken record music - another exploit after an upgrade.
In DeFi, yesterday's patch is tomorrow's exploit, and every upgrade is a roll of the dice.
In a world where code is law, but human error is constant, who's really in control - the devs, the auditors, or the hackers waiting in the wings?

REKT serves as a public platform for anonymous authors, we take no responsibility for the views or content hosted on REKT.
donate (ETH / ERC20): 0x3C5c2F4bCeC51a36494682f91Dbc6cA7c63B514C
disclaimer:
REKT is not responsible or liable in any manner for any Content posted on our Website or in connection with our Services, whether posted or caused by ANON Author of our Website, or by REKT. Although we provide rules for Anon Author conduct and postings, we do not control and are not responsible for what Anon Author post, transmit or share on our Website or Services, and are not responsible for any offensive, inappropriate, obscene, unlawful or otherwise objectionable content you may encounter on our Website or Services. REKT is not responsible for the conduct, whether online or offline, of any user of our Website or Services.
