Paid Network - REKT

What a way to make a living.
Willy Wonka returns with the infinite mint, creating 59,471,745.571 PAID tokens before dumping them onto the unsuspecting Oompa Loompas who were providing liquidity to the PAID/ETH pair on Uniswap.
Total WETH swapped: 2079.603371141493 = $3,104,887.33 Total PAID left in account: 594,717,455.71 = $24,313,147
Total Rugged Amount: $ 27,418,034.33
Banteg tweeted:
I don't know what PAID is, but it looks to me that one founder rugged another.
@n2ckchong’s finding seems to correlate with this suggestion, as he pointed out that “Paid Network's deployer, an EOA, transferred ownership of a contract to the attacker 30 mins before the mint.”
As with most of our cases, it will be almost impossible for the founders to prove that it wasn’t them, leaving the PAID team in a particularly uncomfortable situation.
Perhaps their private keys were compromised…
Kyle Chasse is the CEO of Paid Network, a Youtuber and self-proclaimed “master disruptor crypto OG”. However, even these lofty achievements are not enough to prevent people from suspecting foul play.
Someone out there believes that this was not an exploit, but an inside job.
We usually love it when people slide into the TXID’s, but this note was of a more personal nature than usual.
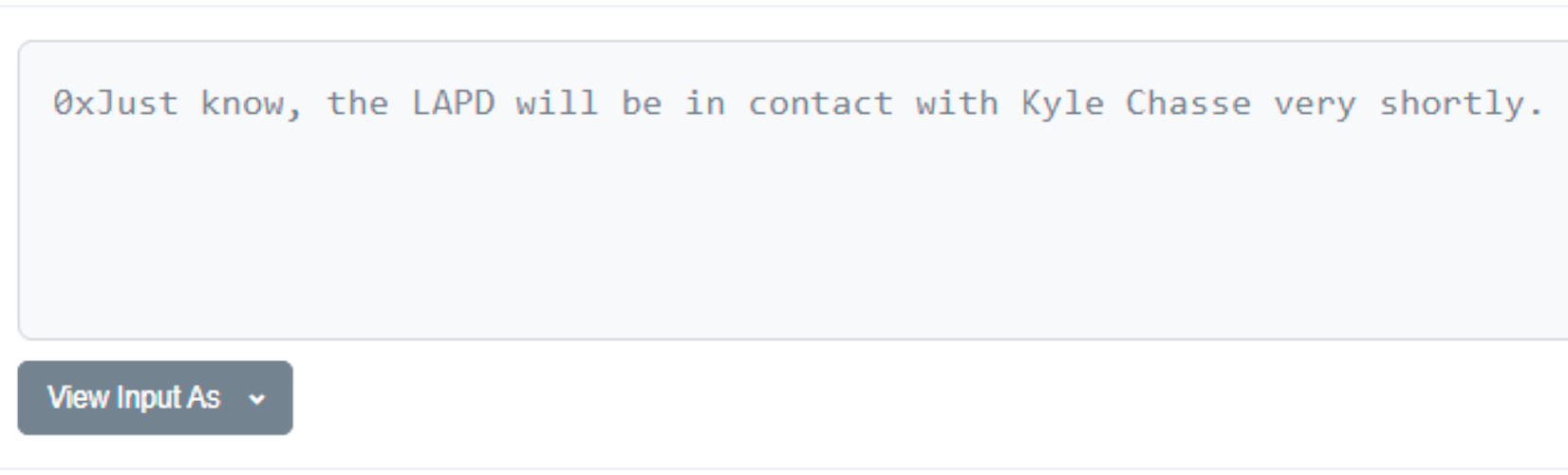
It seems the suspicious sender is not alone in their belief, as we can see that the Twitter account WARONRUGS warned users of this mint capability over a month ago.
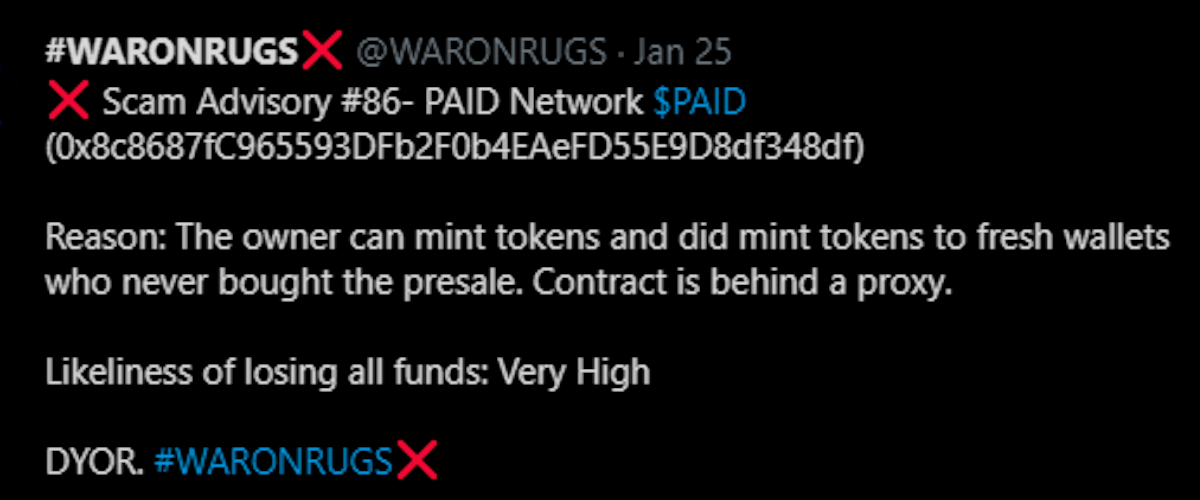
Another message was sent to the minters address to congratulate the “Russian Hackers” for putin in the work.
PSA - If a protocol advertises themselves as a “100x altcoin gem” - it’s probably best to stay clear.
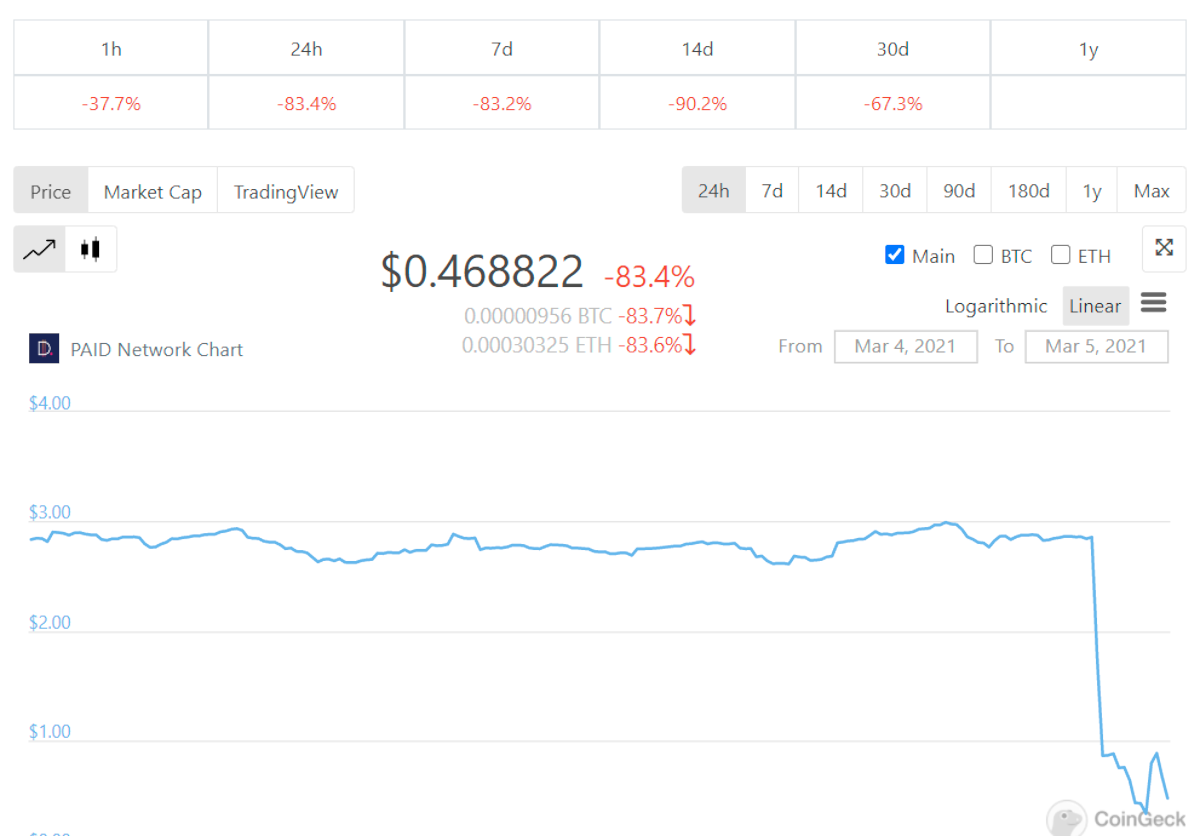
The mint happened just after 18:00 UTC, with the dumping during the next 30 minutes, which took the price of PAID from ~$2.86 to ~$0.32.
PAID Network have tweeted that;
We are investigating the issue. We pulled liquidity, are creating a new smart contract, & will be restoring everyone's original balances to before the hack.
Those with staked, Lpool & UniFarm $PAID will have their tokens be sent to them manually.
We will share more updates soon.

DeFi runs 24/7, a hall of mirrors and back doors where the ruthless walk free.
Working 9-5 is no way to make a living, but is stealing from others any more respectable?
An infinite mint is a magical thing - a golden ticket to make profit illicit, but who’s to blame when the warnings are clear, loot isn’t shared but the responsibility is.
Was this an exploit, a hack or an insider job? We await the official post-mortem from PAID.
Thanks to all the greedy hackers and scammers for keeping us in work.

REKT serves as a public platform for anonymous authors, we take no responsibility for the views or content hosted on REKT.
donate (ETH / ERC20): 0x3C5c2F4bCeC51a36494682f91Dbc6cA7c63B514C
disclaimer:
REKT is not responsible or liable in any manner for any Content posted on our Website or in connection with our Services, whether posted or caused by ANON Author of our Website, or by REKT. Although we provide rules for Anon Author conduct and postings, we do not control and are not responsible for what Anon Author post, transmit or share on our Website or Services, and are not responsible for any offensive, inappropriate, obscene, unlawful or otherwise objectionable content you may encounter on our Website or Services. REKT is not responsible for the conduct, whether online or offline, of any user of our Website or Services.
you might also like...
Tapioca DAO - Rekt
Another day, another private key theft, another protocol rekt. Tapioca DAO on Arbitrum suffers a roughly $4.4 million loss in a private key compromise. Some funds have been recovered, though the full extent of the damage remains to be seen.
Radiant Capital - Rekt II
Radiant Capital gets a $53M haircut. Thought multi-sigs were safe? Think again. Radiant's "robust" 3/11 setup crumbled like a house of cards. Exploited twice in 2024, the future of Radiant looks about as bright as a black hole.
Surviving Digital Danger
Think you've mastered the crypto minefield? Think again. Surviving Digital Danger - The rekt guide to turning paranoia into an art form. It's time to level up your crypto survival skills.
