Zunami Protocol - REKT

NOTE: This article has been edited to remove reference to Ackee Blockchain, who audited an earlier version of the protocol before the attacked MimCurveStakeDAO strategy was added.
The Curve ecosystem can't catch a break…
Yesterday, Zunami Protocol lost $2.1M as the project’s Ether- and USD-pegged stablecoins came under a price manipulation attack.
Although Curve itself was unaffected, the exploiter drained Zunami’s zETH and UZD liquidity pools on Curve, causing the ‘zStables’ to depeg by 85% and 99%, respectively.
Peckshield raised the alarm but, after the recent BlockSec/Curve debacle, was careful not to provoke criticism and opted not to provide transaction hashes or addresses.
Shortly after, Zunami confirmed the exploit:
It appears that zStables have encountered an attack. The collateral remain secure, we delve into the ongoing investigation.
First Conic Finance, then JPEG’D, Alchemix and Curve itself, now Zunami…
Could the Curve Wars be proving even more lucrative for hackers than for protocols?

Credit: Peckshield, BlockSec
Just over an hour after the initial alert, and presumably after confirming no further funds were at risk, Peckshield followed up with more detail:
It is a price manipulation issue, which can be exploited by donation to incorrectly calculate the price as shown in the following figures.
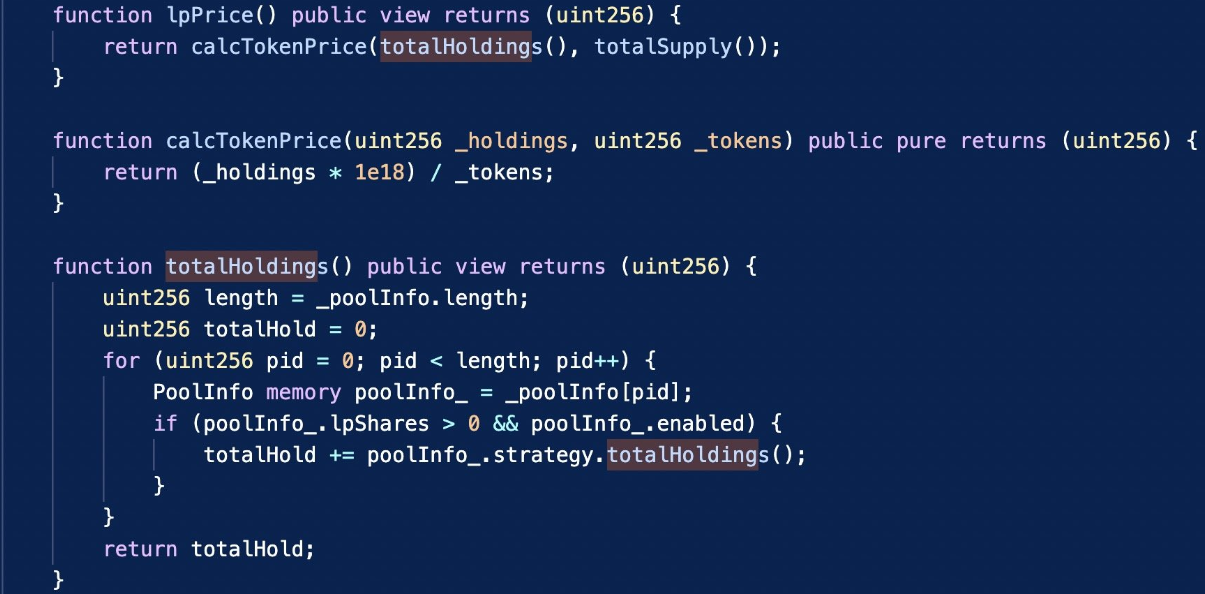
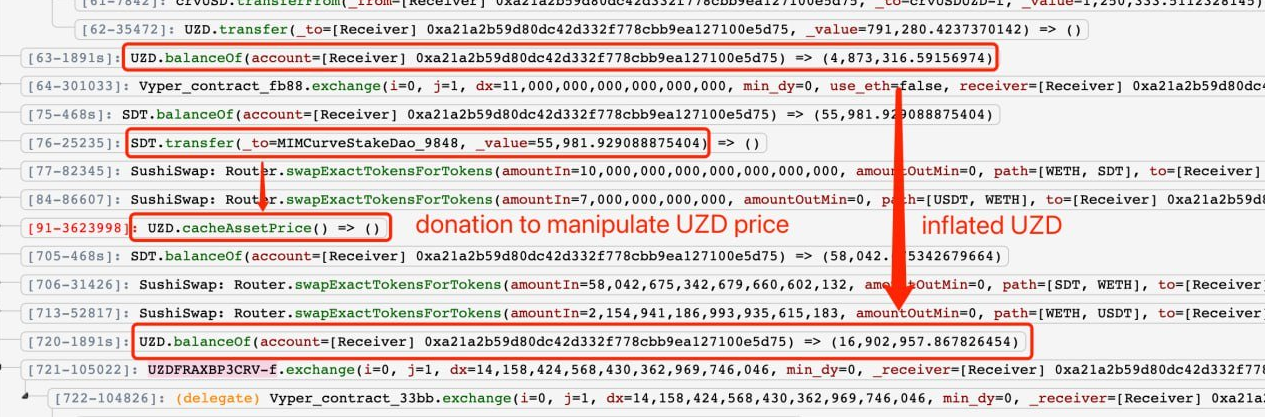
The attacker used flash loans to execute large token swaps (e.g. SDT), causing slippage in the pool which could be used to manipulate LP token prices. The root cause was a flawed price calculation via the totalHoldings function.
BlockSec provided the following step-by-step:

The proceeds (1184 ETH or $2.1M) were quickly deposited into Tornado Cash.
The protocol itself and the UZD and zETH contracts were audited by Hashex.
Attacker’s address: 0x5f4c21c9bb73c8b4a296cc256c0cde324db146df
Exploit tx (zETH): 0x2aec4fdb…
Exploit tx (UZD): 0x0788ba22…
The Sushiswap SDT pool, although used by the hacker during the price manipulation, is safe (despite what a certain relentless bear-poster might like to imply).

Peckshield may have been careful not to include sensitive information in their alert, but others weren’t so cautious.
Following BlockSec’s public announcement of the root cause behind the Vyper bug last month, the backlash prompted a debate about how many security firms apparently chase Twitter clout while potentially aiding hackers.
The discussion, and calls for feedback, appear to have led to tweaked alerting standards which prioritise only the crucial information to alert users who may need to withdraw funds, but without giving away any clues which bad actors may take advantage of.
Another step forwarded is the SEAL 911 hack hotline; the Telegram bot aims to use its list of members is a fast-response for any concerned whitehat looking to alert a potentially vulnerable protocol’s team.
Security teams do important work in DeFi, where exploiters are lurking around every corner.
Not least BlockSec, with their impressive whitehacking record.
But keeping DeFi safe is a constant game of cat-and-mouse, one that can’t always be won.
Who will be next to fall prey?

REKT는 익명 작성자들에 의한 공공 플랫폼이며, REKT에 작성된 관점이나 내용에 대해서 그 어떤 책임도 지지 않습니다.
기부 (ETH / ERC20): 0x3C5c2F4bCeC51a36494682f91Dbc6cA7c63B514C
disclaimer:
REKT는 당사 웹 사이트의 익명의 작성자 또는 REKT에 의해 게시되거나 관련된 서비스에서 게시되는 콘텐츠에 대해 어떠한 책임도 지지 않습니다. 당사는 익명 작성자들의 행동 및 게시물에 대한 규칙을 제공하지만, 익명의 작성자가 웹 사이트 또는 서비스에 게시, 전송 혹은 공유한 내용을 통제하거나 책임지지 않으며, 귀하가 웹 사이트 또는 서비스에서 직면할 수 있는 불쾌함, 부적절함, 음란함, 불법 또는 기타 해로운 콘텐츠에 대해서도 책임을 지지 않습니다. REKT는 당사 웹 사이트 또는 서비스 사용자의 온라인 또는 오프라인 행위에 대한 책임을 지지 않습니다.
추천 기사들......
Zunami Protocol - Rekt II
$500k vanished from Zunami Protocol in a mid-May admin key exploit. Months of stagnant development & perfect timing may have paved the way. Team offered weak excuses, dismissed concerns, left users empty-handed. When emergency keys open doors, who's in control?
Tapioca DAO - Rekt
Another day, another private key theft, another protocol rekt. Tapioca DAO on Arbitrum suffers a roughly $4.4 million loss in a private key compromise. Some funds have been recovered, though the full extent of the damage remains to be seen.
Radiant Capital - Rekt II
Radiant Capital gets a $53M haircut. Thought multi-sigs were safe? Think again. Radiant's "robust" 3/11 setup crumbled like a house of cards. Exploited twice in 2024, the future of Radiant looks about as bright as a black hole.
