Rari Capital - REKT

Young blood and new money.
After a quick break for lunch, it was Rari Capitals turn to get rekt.
The youthful yield aggregator has fallen victim to a serial attacker, as the same wallet which attacked Value DeFi only hours before, turned their eyes onto the Rari Capital ETH pool, removing $10 million worth of ETH.

Rari Capital has attracted attention due to the young age of their developers, causing the community to argue amongst themselves as to whether age is of much relevance when the whole DeFi industry is only 2 - 3 years old.
Although some might say they “had it coming”, we take no pleasure in learning that people have lost their money.
There are no developers with 10 years experience in DeFi system design, this is a meritocracy that depends on the skill and maturity of the person rather than the length of their CV.
Each attack presents us with a valuable lesson, and we must study the techniques in order to build a safer future.

We’re looking at the actions of a cross-chain killer, who used the blood money from Value DeFi to fuel their attack on Rari Capital.
5,346 BNB ($3.8M) were stolen and swapped to 1k ETH.
The attacker’s actions on BSC were as follows:
1: Create a fake token and pool it with BNB on PancakeSwap in order to use Alpaca Finance.
2: Interact with Alpaca Finance, where when calling approve() for a fake token, a payload is called, which allows an attacker to use VSafe through Codex farm to get vSafeWBNB
3: Convert vSafeWBNB to WBNB
4: Transfer WBNB to Ethereum through Anyswap.
Repeat 2x.
The attack on Rari was as follows:
1: Create a fake token and pool with it on SushiSwap
2: Interact with Alpha Homora, where a payload is also called so that the attacker can get ibETH in the Rari ETH pool contract.
3: Convert ibETH to ETH in the Rari ETH pool.
As a result, 2.9k ETH ($11.1M) was stolen, and another 1.7k ETH was at risk before the actions of the Rari team.
The total profit from the two attacks was $15M in ETH.
credit: frankresearcher
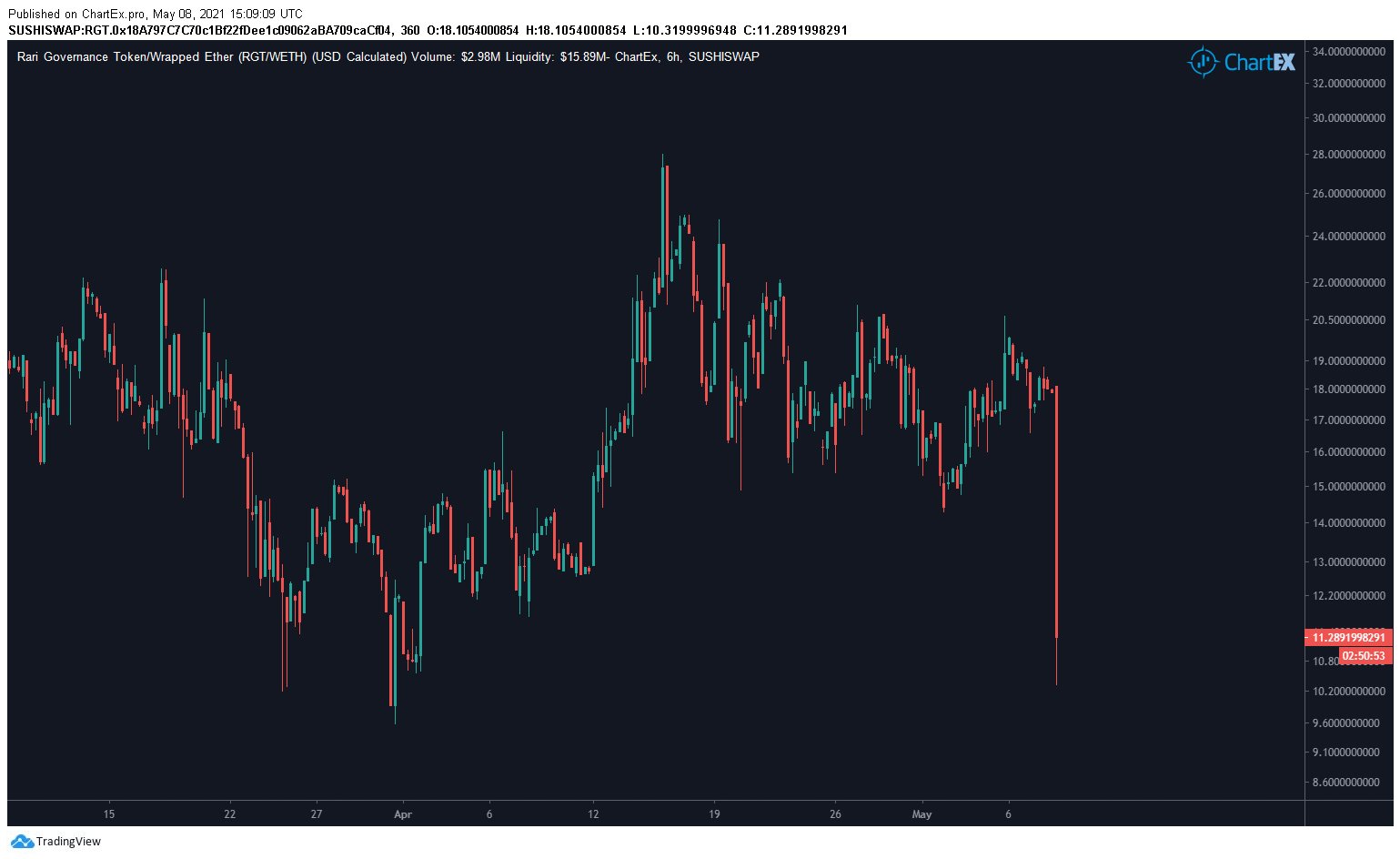
The Rari Capital governance token $RGT fell sharply in price following the attack.
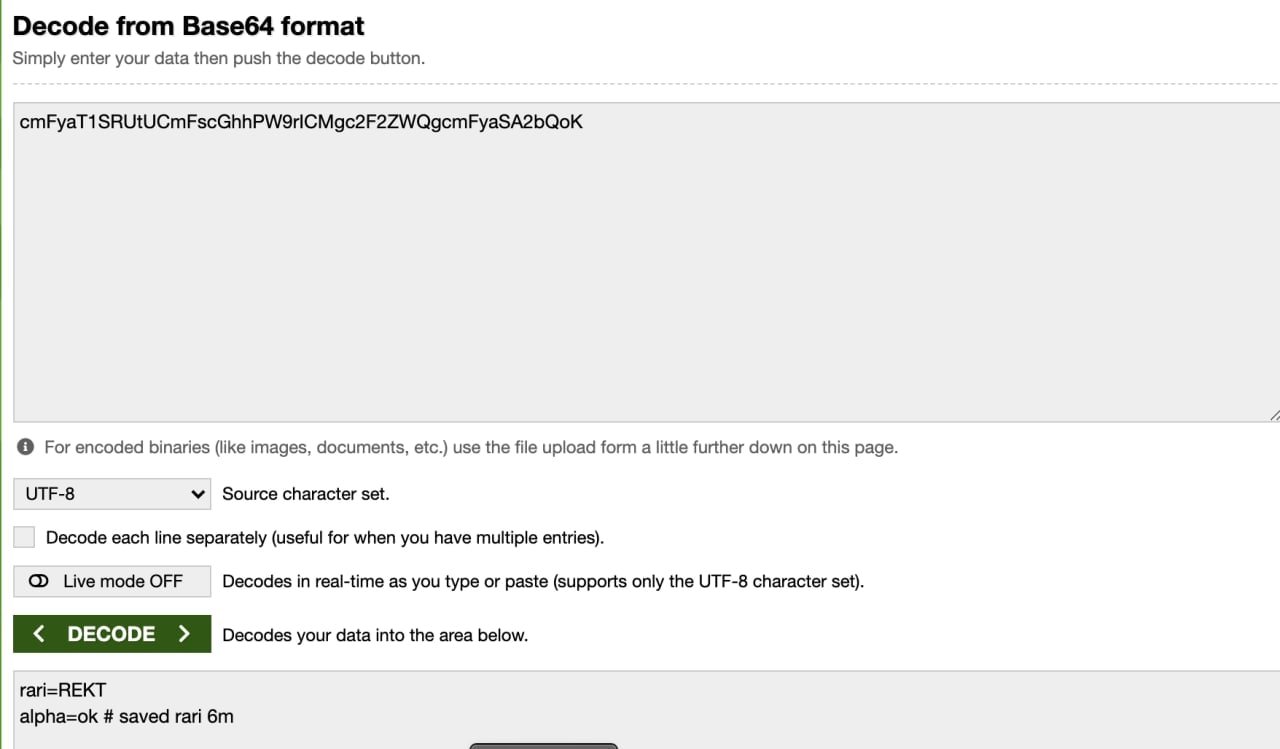
The attacker decided to voice their opinion on the involved protocols, but it seems they had second thoughts, as they tried to cancel the transaction. However, they set the gas too low and the cancellation didn’t go through for 20 minutes, giving everyone time to see their message.

This attack technique was similar to the Evil Pickle Jar, one which looks likely to become even more common in the future.
Even though various protocols were used, the same exploit mechanism was applied.
Alpaca/Alpha, vSafe/Rari, PancakeSwap/SushiSwap - the interaction between them was built in such a way that the exploit was easily repeated on another chain.
The interoperability between DeFi protocols is increasing, and the blurred lines make for even easier escape routes.
In the roaring twenties, the ruthless are rewarded, and any prosecution seems unlikely.
With so many other surface-level crimes in crypto, who’s going to try and prosecute someone for exploiting contracts where so many remain anonymous?

REKT는 익명 작성자들에 의한 공공 플랫폼이며, REKT에 작성된 관점이나 내용에 대해서 그 어떤 책임도 지지 않습니다.
기부 (ETH / ERC20): 0x3C5c2F4bCeC51a36494682f91Dbc6cA7c63B514C
disclaimer:
REKT는 당사 웹 사이트의 익명의 작성자 또는 REKT에 의해 게시되거나 관련된 서비스에서 게시되는 콘텐츠에 대해 어떠한 책임도 지지 않습니다. 당사는 익명 작성자들의 행동 및 게시물에 대한 규칙을 제공하지만, 익명의 작성자가 웹 사이트 또는 서비스에 게시, 전송 혹은 공유한 내용을 통제하거나 책임지지 않으며, 귀하가 웹 사이트 또는 서비스에서 직면할 수 있는 불쾌함, 부적절함, 음란함, 불법 또는 기타 해로운 콘텐츠에 대해서도 책임을 지지 않습니다. REKT는 당사 웹 사이트 또는 서비스 사용자의 온라인 또는 오프라인 행위에 대한 책임을 지지 않습니다.
추천 기사들......
Locked Away
From teen DeFi heroes to SEC villains. How Rari Capital suffered two devastating hacks, got charged with fraud, and vanished - leaving a graveyard of frozen funds and a lesson in what happens when code meets hubris.
Tapioca DAO - Rekt
Another day, another private key theft, another protocol rekt. Tapioca DAO on Arbitrum suffers a roughly $4.4 million loss in a private key compromise. Some funds have been recovered, though the full extent of the damage remains to be seen.
Radiant Capital - Rekt II
Radiant Capital gets a $53M haircut. Thought multi-sigs were safe? Think again. Radiant's "robust" 3/11 setup crumbled like a house of cards. Exploited twice in 2024, the future of Radiant looks about as bright as a black hole.
