EraLend - REKT

One more added to the list.
Yesterday, EraLend, a lending platform on zkSync Era, lost $3.4M to the rampant read-only reentrancy bug plaguing protocols across the cryptosphere.
The alarm was raised and the losses stacked up. Syncswap was keen to reassure their users that they were not at risk, though recommended pulling LP tokens from EraLend as a precaution. In the end, only USDC deposits on EraLend were affected.
This is the second leaderboard entry to come from zkSync, after Merlin DEX’s $1.8M rugpull in April.
With hack szn hotting up, where will be hit next?

Credit: Spreekaway, Peckshield
Read-only reentrancy is nothing new, with last Friday’s attack on Conic Finance the latest in a long line of projects rekt by the issue.
In EraLend’s case, the attacker was able to exploit the vulnerability via a callback when burning LP tokens.
in the syncswap LP tokens, one can burn, then callback before update_reserves is called. so the oracle uses an incorrect reserves value to calculate the price, resulting in an inflating oracle price.
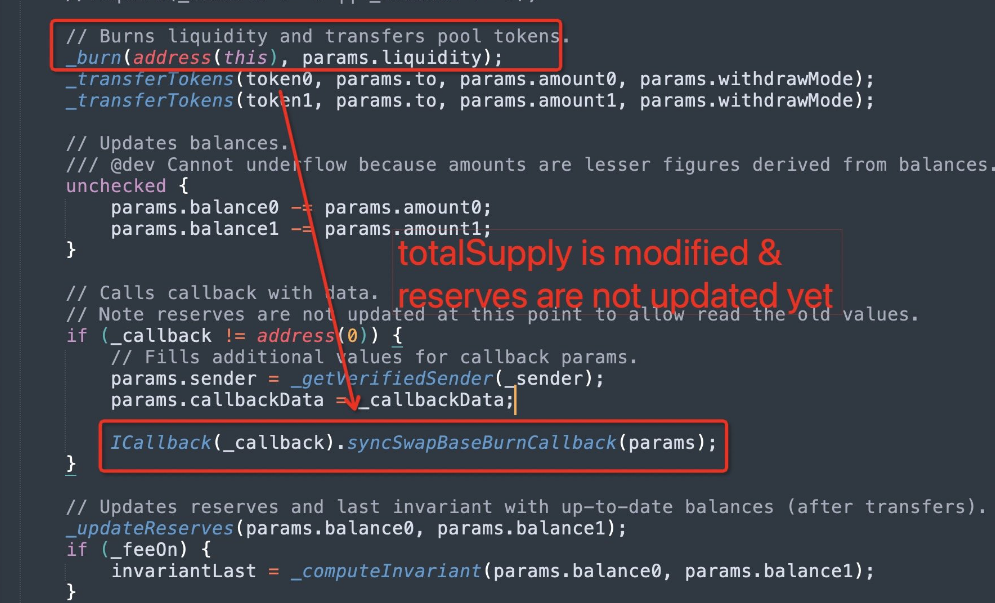
The buggy code was recycled from SyncSwap, but improperly implemented. Astonishingly, the code even contained the comment pointing out the potentially risky routine, which was apparently ignored:
Note reserves are not updated at this point to allow read the old values.
But comments are not effective reentrancy protection.
Exploiter address: 0xf1D076c9Be4533086f967e14EE6aFf204D5ECE7a
Example attack txs: 0x7ac4da1e…, 0x99efebac…
Of the $3.4M lost from EraLend, Hacken puts the attacker profits at around $2.66M and traced funds to addresses on ETH, ARB and OP.

BlockSec tweeted a warning to other projects that may be using the same code:
Alert! All projects that rely on the following Syncswap code need to be vigilant.
But given the prevalence of this attack type over the last months, why haven’t all devs already double (or triple) checked by now?
Peckshield, who audited EraLend (then Nexon Finance) in March, washed their hands of responsibility. The audit apparently “assumes a trusted price oracle”, simplifying their job by simply ignoring one of the trickiest and most exploitable parts of many DeFi protocols.
As noted by ChainSecurity’s Matthias Egli at EthCC last week, the losses from this string of hacks is far lower than the potential losses from far larger protocols that had been vulnerable before the vector was discovered last year.
But that silver lining likely doesn’t make much difference to EraLend users.
How long until this bug strikes again?

REKT는 익명 작성자들에 의한 공공 플랫폼이며, REKT에 작성된 관점이나 내용에 대해서 그 어떤 책임도 지지 않습니다.
기부 (ETH / ERC20): 0x3C5c2F4bCeC51a36494682f91Dbc6cA7c63B514C
disclaimer:
REKT는 당사 웹 사이트의 익명의 작성자 또는 REKT에 의해 게시되거나 관련된 서비스에서 게시되는 콘텐츠에 대해 어떠한 책임도 지지 않습니다. 당사는 익명 작성자들의 행동 및 게시물에 대한 규칙을 제공하지만, 익명의 작성자가 웹 사이트 또는 서비스에 게시, 전송 혹은 공유한 내용을 통제하거나 책임지지 않으며, 귀하가 웹 사이트 또는 서비스에서 직면할 수 있는 불쾌함, 부적절함, 음란함, 불법 또는 기타 해로운 콘텐츠에 대해서도 책임을 지지 않습니다. REKT는 당사 웹 사이트 또는 서비스 사용자의 온라인 또는 오프라인 행위에 대한 책임을 지지 않습니다.
추천 기사들......
Kannagi Finance - REKT
Kannagi Finance, a yield aggregator on zkSync pulled the rug on Saturday, dropping TVL from $2.1M to $0.17. The auditors may have highlighted 'centralised aspects' but, in this industry, who reads the fine print?
Merlin DEX - REKT
$1.8M disappeared in a puff of smoke as Merlin pulled the classic DeFi magic trick. The zksync-native DEX had just completed its audit with Certik. How can such an easily ruggable protocol be green-lit? Or are users also to blame?
Tapioca DAO - Rekt
Another day, another private key theft, another protocol rekt. Tapioca DAO on Arbitrum suffers a roughly $4.4 million loss in a private key compromise. Some funds have been recovered, though the full extent of the damage remains to be seen.
