Indexed Finance - REKT

That’s one more protocol added to the rekt register, and $16 million more on our leaderboard.
We’ll always bring our stories to Twitter, but if you want to talk directly to the characters involved, then the best place for you is the rekt.news Telegram group.
Shortly after the attack, Indexed Finance core contributor and rekt reader Dr Laurence Day showed the rekt group members as he tried to communicate with the hacker on-chain;
Indexed Finance here.
Time to talk?

Indexed Finance offers investors 6 indices, each one a pool of various assets. Each index pool has its own token whose price should be a weighted average of the underlying assets.
At 18:37 UTC on October 14th, an attack took place targeting the DEFI5 and CC10 pools. The “Future of Finance Fund” (FFF) was also heavily affected, given that DEFI5 and CC10 tokens make up 37.05% of its underlying assets.
More details of the exploit can be found in the official post-mortem as well as in Mudit Gupta’s twitter thread.
Dillon Kellar; the sole developer responsible for writing the original code of Indexed Finance, has made his thoughts public in a Tweet thread.
The code governing the index pools is forked from the Balancer Pool contract. This allows for the internal rebalancing of assets within the pool on a constant product curve.
The function extrapolatePoolValueFromToken is based on the “first token in the pool with a target weight over 0 and which is fully initialized” to calculate the total value of the pool.
total_value = token_balance * total_weight / token_weight
In order to control slippage, the rate at which the resulting changes in weights are enacted within the pool is limited, creating a temporary discrepancy ripe for manipulation.
The attacker’s address was funded via Tornado Cash hours before the attack: 0xba5ed1488be60ba2facc6b66c6d6f0befba22ebe
Both the DEFI and CC10 pools were attacked in the same way, see this transaction for the attack on the DEFI5 pool.
The attacker was able to take advantage of the above by using flash loans of the other assets in the pool to buy out UNI, decreasing the extrapolated value due to the delay in updating UNI’s weight decrease.
This was done gradually, as the “pool does not allow swaps to send more than 1/2 of the pool’s existing balance in a token or purchase more than 1/3 of the pool’s balance in a token”.
After calling the updateMinimumBalance function using the gamed pool value, the controller valued the pool at just 29,851 SUSHI (~$300k), “despite the pool having received over a hundred million dollars worth of other assets”.
Once prepared, the attacker could deposit relatively small amounts of (now heavily over-weighted) SUSHI into the pool, minting a massively inflated number of DEFI5 tokens in return.
These were subsequently cashed out for the assets in the pool.
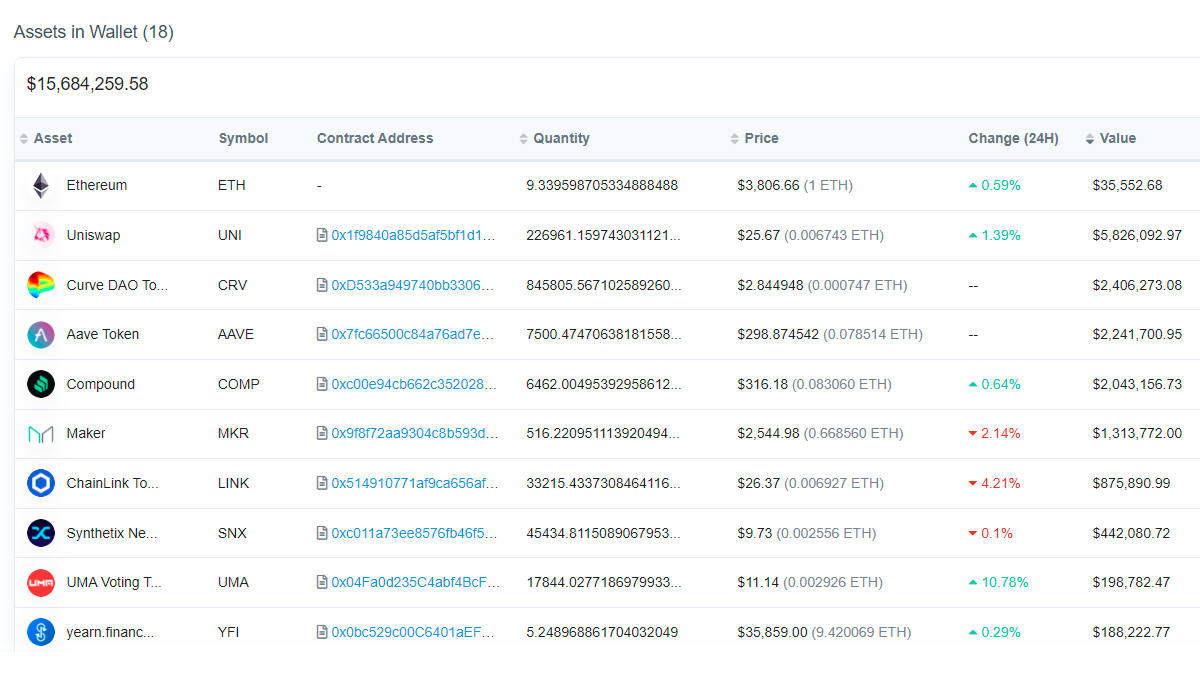
In total, about $16M of a variety of assets were stolen by the attacker, at the time of writing they remain in this address.
In a follow up to the official post-mortem, Doctor Day has put out a statement:
The knife twist is that we've realised that we believe that we actually know who did this: we spoke to them quite a bit prior to the execution of this attack.
Starting on the 15th of September, we were approached by a Discord user under the name 'UmbralUpsilon' (currently BogHolder#1688), asking some questions about the way in which certain parameters were utilised in the oracle. Since every component of Indexed is open-source, we answered these questions, and upon asking the reason, were told that they were attempting to create an arbitrage bot for the pools.
This is a key part of how Indexed generates revenue (exit fees on burns when arbitraging the NAV of tokens and their value on DEXes), and we were happy to engage with queries about the mechanics, explaining how reindexes work, the timing of reweights, how tokens are added and removed from candidate asset lists, and so on. We had no reason to be alarmed: all of these conversations were in the spirit of open-source collaboration.
We are aware (courtesy of @pcaversaccio) that the exploiter requested some Kovan testnet Ether via Gitter, using the (dead, presumably created for the purposes of the assault) Twitter account @ZetaZeroes. We have reached out to them via Gitter with the following message.
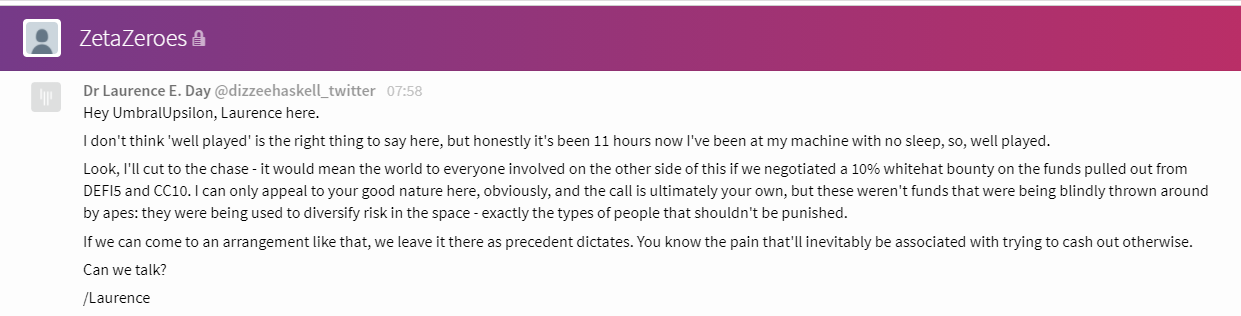
We speak now directly to the exploiter, if they ever read this: you’re clearly incredibly skilled: this is something that has been overlooked for ten months in production, and you’re the only one that found it. While it would have been so much more productive for you to instead choose to work with us: be the antihero of this story rather than the villain. Take a 10% whitehat, and save a lot of people the effort of engaging law enforcement.
The people that are affected by this are those that are trying to diversify risk within a volatile space. That’s part of what makes this particularly cruel: no one deserves to have their funds whisked away, but the context here is an irony that can’t be ignored.
Our door’s open, and it’ll make a much more satisfying footnote to our appearance on rekt.news.

Wise words from the Doxxed Doctor, who’s been put in the hot seat through no fault of his own.
The damage dealt by these attackers is not just financial.
No DeFi developer should have to receive death threats.
Is anonymity the only way to stay safe?

REKT serves as a public platform for anonymous authors, we take no responsibility for the views or content hosted on REKT.
donate (ETH / ERC20): 0x3C5c2F4bCeC51a36494682f91Dbc6cA7c63B514C
disclaimer:
REKT is not responsible or liable in any manner for any Content posted on our Website or in connection with our Services, whether posted or caused by ANON Author of our Website, or by REKT. Although we provide rules for Anon Author conduct and postings, we do not control and are not responsible for what Anon Author post, transmit or share on our Website or Services, and are not responsible for any offensive, inappropriate, obscene, unlawful or otherwise objectionable content you may encounter on our Website or Services. REKT is not responsible for the conduct, whether online or offline, of any user of our Website or Services.
