Ape Season Returns
The apes are out of their cages once more.
Just over a year ago, the collapse of FTX (followed by SBF’s accompanying meltdown) finally put the nail in last cycle’s coffin.
As a result, many predicted, or even declared, the death of the crypto industry, which had so publicly crashed and burned after flirting with mainstream acceptance.
While crypto’s former heroes confront the consequences of their hubris, reduced to cutting deals in tinned fish rather than unsecured credit, the first signs of markets heating up has sent dormant degens into a FOMO frenzy.
But familiar dangers are ever-present for apes on the loose.
A seemingly unending stream of often widespread exploits, barefaced ponzi-layering, chains pushed to their limit and an out-of-control phishing landscape all lay in wait for the unsuspecting simian.
While much has been achieved by teams working hard through the bear market, it seems each innovation has also spawned additional ways to get rekt in the cryptosphere.
Has nothing changed?

Recent widespread security hazards have provided repeat opportunities to pay the ape tax.
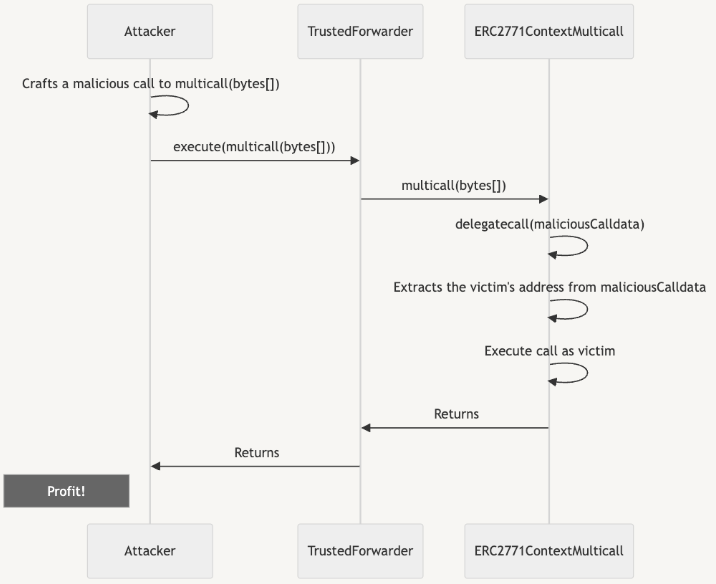
First, plug-and-play smart contract toolkit Thirdweb disclosed a vulnerability related to the use of ERC-2771 alongside multicall which allowed for “address spoofing via malicious calldata in forwarded requests”.
Although the specific vulnerability was not disclosed, Thirdweb listed the 27 out-of-the-box contracts affected, giving potential black hats a convenient shortlist to explore…
According to ScamSniffer, over 500 mainnet and over 1000 BSC token contracts had used the dangerous Thirdweb code. Over the following days reports of projects being exploited trickled through.
Picking-off stragglers is seemingly an ongoing sport.
OpenZeppelin followed the initial disclosure up with a detailed post-mortem, explaining that “the issue is not particular to the implementations contained in the OpenZeppelin Contracts library”, but is a problem arising from a particular integration between the two standards.
The report includes the following example attack flow as well as instructions on how to secure affected contracts:
Next came what, at the time, seemed an existential threat to what was once seen as the gold standard of self-custody.
Reports of strange behavior on multiple front-ends caused rumour, suspicion and fear to spread like wildfire.
An hour later, the issue was identified as a wallet drainer (Angel) injected into Ledger’s connect-kit code, which is used by many project’s front-ends to connect wallets via the connect-kit loader.
The npm package (now fixed) used by the connect-kit had been updated to include the wallet drainer script, which was now being served to users upon connecting their wallets to any of 290 instances of the vulnerable code across the ecosystem.
The malicious versions were removed and the issue was patched two hours after the first reports began to circulate, and around four hours after the drainer script was added (though hints had been left an hour earlier still).
In the end, what may have been the industry’s most wide-spread and deepest-seated phishing vector netted just $600k.
Ledger has since committed to reimbursing the losses, as well as deprecating Blind Signing within six months, though it remains to be seen if this is viable…
Far greater damage was dealt to Ledger’s (already faltering) reputation, however.
Unbelievably, a company who’s entire brand is built on security and safety allowed a former employee’s phished credentials to instantly start serving drainer scripts to end users all across the ecosystem.
It must be said that, despite OpSec failures from within Ledger, DeFi front-ends might want to stay away from web2 efficiency models when security should be the number one concern.
Even if individual projects are to take some of the blame, after multiple scandals will Ledger ever be able to Recover their user’s trust?
Lastly, over the weekend, came the Ape-ocalypse:
If you've ever used NFT Trader in the past, revoke approval to their contract ASAP (0x13d8faF4A690f5AE52E2D2C52938d1167057B9af)
So far already 37 BAYC and 13 MAYC have already been drained to this address
The great ape escape saw assets totalling at least $4M lost to a reentrancy attack, which took advantage of existing approvals via a maliciously crafted self-swap.
Things took a bizarre turn when the exploiter (who claimed to be a ‘good person’, whilst claiming and dumping victims’ APE staking rewards) decided to ransom the NFTs back to victims:
...if you want the monkey nft back, then you need to pay me a bounty, which is what I deserve
1 BAYC = 30 ETH 1 MAYC = 6 ETH you need to pay me %10 ETH for my work…
…After you send me the reward, I'll return the monkey to you, with the caveat that you'll need to unauthorize the exploit contract…
...Finally, I wish you all a happy day!
Luckily, a keen eye spotted a way to thwart copycat attempts to steal the remaining NFTs, with a rescue operation executed, placing some of the stolen goods directly back into victim wallets.
Hopefully those who managed to revoke their approvals had already refreshed their browser cache.
Shortly after the apes had been returned to their cages, however, another attack saw Flooring Protocol exploited via a vulnerability which had been introduced during a recent upgrade.

Despite the relatively modest financial damages, these three incidents have served to underline just how delicate and interdependent the DeFi ecosystem can be.
And for users, as FOMO takes over, hopefully they serve as timely reminders to stay vigilant and never keep active approvals for high-value assets.
All part of the joys of self-custody.
But while there are essentially endless ways to get rekt on-chain, or through the ever-evolving phishing campaigns relentlessly taking advantage of web2’s blindspots, the supposed safety offered by centralised systems is far from certain.
Recent centralised exchange hacks aside, CeDeFi has seemingly been up to the type of dirty tricks which would be unlikely to escape scrutiny on mainnet.
BSC has long been the apes’ favourite enclosure in this crypto zoo, but a closed-source hard-fork shows that they aren’t playing by the same rules as other chains. And, although rugging the BNB Bridge hacker doesn’t seem morally wrong, it does set a dangerous precedent.
In other news, OKX, whose recently-rekt DEX aggregator lost $2.7M last week, has been alerted to a critical bug in its wallet which allowed for remote code execution.
And rather than concentrating on keeping users safe, clout-chasing auditors Certik decided it would be best to shout about their findings, drawing extra attention from would-be exploiters.

Despite all the risks, opportunity certainly is out there.
Solana SZN is bringing back bull market levels of degeneracy, apparently having escaped its previous close-association with SBF and FTX.
The Jito drop kicked off the mania, as users with as little as 100 points (e.g. staking 1 SOL x 100 days) received almost 5k JTO, worth almost $10k at the time, and >$20k two days later.
Elsewhere, earning 4.5% plus ‘points’ for trusting >$800M to a (Paradigm-backed) multisig, re-staking and ponzi-layering, chain-breaking inscriptions fever…
There are plenty of places to YOLO any funds remaining after a brutal 18 months, and some of them will undoubtedly prove to have been lucrative options.
And as retail traders ape in once again, anyone with even a modest audience is poised to rug their followers, hoping to claw back some of their bear-market losses.
In the background, the regulatory slugfest continues, but, with ETF hype building, it now feels more like clutching at straws than scorched earth.
However, the terrorist financing narrative has contributed to a renewed vigor.
Recent developments, such as Tether’s u-turn overturning their previous decision not to pre-emptively freeze USDT on OFAC-sanctioned addresses, as well as working alongside the FBI show that, this cycle, US authorities will have more of a foothold before the madness really kicks off.
While this may help crypto’s image as dirty money, other, more generalised, intel-gathering operations are also in the works.
Binance’s recent deal will also mean extensive monitoring from within, something that the EU sees potentially viable even in DeFi.
If we hope to avoid becoming a financial surveillance tool, we will have to start taking self-policing seriously.
But some things never change.
As we make our Return to the Planet of the Apes, will we continue to ‘disrupt’ and ‘innovate’, pushing towards the future of finance?
Or will we simply build another house of cards, unwittingly setting ourselves up to crash and burn once more?
Is there even a difference?

REKT serves as a public platform for anonymous authors, we take no responsibility for the views or content hosted on REKT.
donate (ETH / ERC20): 0x3C5c2F4bCeC51a36494682f91Dbc6cA7c63B514C
disclaimer:
REKT is not responsible or liable in any manner for any Content posted on our Website or in connection with our Services, whether posted or caused by ANON Author of our Website, or by REKT. Although we provide rules for Anon Author conduct and postings, we do not control and are not responsible for what Anon Author post, transmit or share on our Website or Services, and are not responsible for any offensive, inappropriate, obscene, unlawful or otherwise objectionable content you may encounter on our Website or Services. REKT is not responsible for the conduct, whether online or offline, of any user of our Website or Services.
you might also like...
Blood on the Blockchain
The co-founder of Ledger - David Balland’s severed finger, a $10 million ransom, and a 48-hour manhunt. This isn’t a Netflix thriller - it’s a brutal reminder that the lines between wealth and survival can be dangerous in crypto.
Recover - Ledger's Latest L
Ledger’s new firmware update has the crypto crowd in crisis. The announcement of the new Recover service has many asking questions about the capabilities of the devices, which run on closed-source code. Trust me bro.
